~lobsters | Bookmarks (2102)
-
Matching Regexps 200 Times Faster
Written by Benoit Daloze @eregontp on March 14, 2025 TLDR: Regular Expressions can be faster than...
-
Shellcode Encoded in UUIDs - SANS Internet Storm Center
I returned from another FOR610[1] class last week in London. One key tip I give to...
-
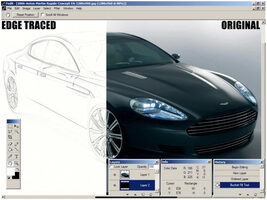
That time I recreated Photoshop in C++ • F055
As I’m getting older I look back on all the things I’ve done as a creative...
-
Decoding JSON sum types in Go without panicking
14 March, 2025 The Go programming language doesn't have native support for sum types, but we'll...
-
Is your Rails application special?
Legacy Rails applications can be unpredictable, so never assume anything about their behavior. The first step...
-
did u ever read so hard u accidentally wrote?
Owning a production Postgres database is never boring. The other day, I’m looking for trouble (as...
-
A look at Firefox forks [LWN.net]
This article brought to you by LWN subscribers Subscribers to LWN.net made this article — and...
-
An introduction to Magit, an Emacs mode for Git
Magit is the sweetener that masks the bitter taste you get when you have to commune...
-
What are you doing this weekend? | Lobsters
Feel free to tell what you plan on doing this weekend and even ask for help...
-
Enhancing CA Practices: Key Updates in Mozilla Root Store Policy, v3.0 – Mozilla Security Blog
Mozilla remains committed to fostering a secure, agile, and transparent Web PKI ecosystem. The new Mozilla...
-
Typestate Programming - The Embedded Rust Book
The concept of typestates describes the encoding of information about the current state of an object...
-
What Programming Concepts do you Struggle to Grok or Use in Production? | Lobsters
For me, type magic whether Haskelly or Idrisy dependent types evades me. A lot of modern...