~lobsters | Bookmarks (1992)
-
"A Story About Jessica" by SwiftOnSecurity
The cybersecurity expert SwiftOnSecurity, a decade ago, wrote a parable called "A Story About Jessica" and...
-
CWE - 2023 CWE Top 25 Most Dangerous Software Weaknesses
Over the span of the last five publications of the CWE Top 25 Most Dangerous Software...
-
Pulling Linux up by its bootstraps [LWN.net]
The following subscription-only content has been made available to you by an LWN subscriber. Thousands of...
-
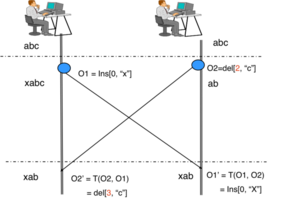
Once more about the rule of 5
Arne Mertz talked about misused guidelines at C++OnSea. Among those, there was the rule of 5....
-
Racket Survey 2024
If you have used Racket, or you are considering using Racket, please help us by completing...
-
Conditional logging with query parameters
Another post, another chance to talk about a pattern I’ve been using quite a while but...
-
Generating YAML files with Nix — kokada
I hate YAML. Instead of writing an essay on why I hate YAML, I can just...
-
Release 0.15 · Foxboron/sbctl
The landlock feature is run with "best effort" and will degrade it's feature set on unsupported...