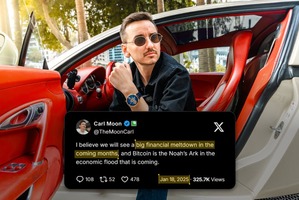
Carl “Moon” Runefelt Predicted the Market Crash — And It’s Happening Now
Carl “Moon” Runefelt warned of a market crash in January 2025—and it’s happening now. Using trends...

Meet Neo Auth, Peris.ai, and Midas Analytics: HackerNoon Startups of the Week
Each week, the HackerNoon team highlights standout Startups from our Startups of The Year database. Every...

A New AI Tool Builds Knowledge Graphs So Good, They Could Rewire Scientific Discovery
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Scientists Built a Smarter, Sharper Materials Graph by Teaching AI to Double-Check Its Work
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Meet the HackerNoon Top Writers: Writing Through the Noise of AI with Albert Lie
Meet Albert Lie, Co-Founder & CTO of Forward Labs, in his interview with HackerNoon Writers Spotlight,...

AI Model Reads Thousands of Studies, Nails Battery Science Better Than Expected
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Scientists Built a Knowledge Graph for Materials—And You Can Actually Use It
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Scientists Built a Smart Filter for Science Papers—and It’s Cleaning Up the Data Chaos
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

AI-Generated E-Books Are Polluting the Internet With Robotic Rubbish—And Readers Aren’t Buying It
The Kindle store is flooded with auto-generated e-books written by AI authors. The content is hollow....

This AI Doesn’t Just Skim Scientific Papers—It Tags, Sorts, and Explains Them Too
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

This AI Reads Science Papers Like a Pro, Even When Humans Can’t Agree on the Words
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Researchers Build AI Knowledge Graph That Sifts Through Science Papers For You
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Tired of Sifting Through Science Papers? This AI Knowledge Graph Does It for You
This paper presents a new AI-powered knowledge graph that organizes real-world materials science research into an...

Cut Your MongoDB Costs by 79% with Shape‑First Optimizations
A fictional startup’s MongoDB bill spiked 20% when Atlas auto‑scaled to an M60. By profiling slow...

Why I Chose 60 Lines of JavaScript Over NestJS for a Budget Project
When building an API for a tiny startup on a shoestring budget, the author compares raw...

The TechBeat: Hallucinations by Design - (Part 3): Trusting Vectors Without Testing Them (4/18/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...

TnT-LLM: LLMs for Automated Text Taxonomy and Classification
This paper presents TnT-LLM, a framework leveraging LLMs to automate large-scale text analysis, including label generation...

TnT-LLM: Automating Text Taxonomy Generation and Classification With Large Language Models
We begin with a high-level overview of TnT-LLM, our proposed two-phase framework for 1) LLM-powered taxonomy...

Batched Prompting for Efficient GPT-4 Annotatio
This section outlines the Batched Prompting approach used to annotate preferences efficiently with GPT-4, where all...
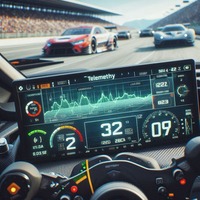
How to Set Up Simhub With Gran Turismo 7
Gran ==Turismo== 7 (==GT7==) game data can now be accessed with standard networking protocols. Telemetry data...

Understanding Concentrability in Direct Nash Optimization
In this section, we provide detailed theoretical proofs supporting the Direct Nash Optimization (DNO) framework. The...

xAI’s Grok 3: All the GPUs, None of the Breakthroughs
Elon claimed Grok 3 was the world's best AI. Two months later, how does it really...

Extending Direct Nash Optimization for Regularized Preferences
This section presents an extension of the Direct Nash Optimization (DNO) framework for handling regularized preferences....

What Does the Future of AI Model Training Hold?
This section details Direct Nash Optimization (DNO), a method designed to optimize LLMs using Nash equilibrium...

Is AI Trading the Answer to Crypto Market Volatility?
AI is becoming essential in crypto trading, automating decisions, reducing risks, and unlocking 24/7 arbitrage opportunities...

Skeptical Engineer Tries AI Coding Agent, Walks Away a Believer
The "stdlib" approach to agent engineering is a way to teach a new engineer how to...

Excel DAYS Function Explained: Calculating Date Differences Between Two Dates!
DAYS function in Excel is used to calculate the number of days between two dates. The...

Rust’s Build.rs Might Be the Most Underrated Feature in Cargo
how to automate Rust build customization using Cargo metadata and a build script—ideal for projects needing...

The Testing Hack That Makes Bugs Easier to Catch (and Code Easier to Read)
Table-driven testing simplifies how we test multiple input-output cases by organizing them like data rows.

This New Stablecoin Claims It Can Earn You Yield Without the Risky Crypto Shenanigans
Stablecoins are big in crypto, but earning good, stable returns is tricky. CAP Money is a...

Why Copper and P2P.org Could Redefine Institutional Crypto Staking Forever
Copper partners with P2P.org to deliver advanced staking solutions, merging cutting-edge custody technology with institutional-grade infrastructure.
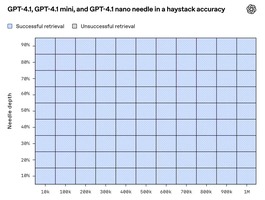
GPT-4.1's 1M-token Context Window is Impressive but Insufficient for Real-world Use Cases
OpenAI announced GPT-4.1, featuring a staggering 1M-token context window and perfect needle-in-a-haystack accuracy. As the founder...

Next Time You Prompt, Try Engineering it
The AI toy box trend exploded online, but most of what I saw was prompted for...

How One PM Replaced a Junior Dev with ChatGPT and Built Three Bots in a Week
AI tools—particularly code-generating assistants like Cursor and Claude—are enabling non-developers to independently build tools they need.

5 Ways Artificial Intelligence Can Help Democratize Access to Quality Education
Several reasons prevent universal access to quality education, and technology has tried to bridge the gap...

No More Dark Patterns: New Laws Are Forcing Streaming and Apps to Play Fair
Many common growth hacks used by Subscription-based businesses are under regulatory fire worldwide. This article talks...

How to Cash 300K Requests per Second in a High-Volume Surveillance System
eBPF is a Linux technology that allows small, high-performance programs to run directly inside the kernel....

Google, AWS, and Azure Are Done Letting Vendors Break Their AI Servers
Cloud companies can't afford to treat AI hardware like traditional infrastructure. The new game is proactive,...

Building a Multi-Language Monster Pipeline? Here’s the Smart Way to Do It
Instead of forcing every team or process to use the same tech stack, build a modular,...

Tech Stack Decisions are Make-or-break for Startups
Lean Tech Stack is a minimalist approach to selecting and using technologies aimed at optimising the...

How Primary Committee Size Impacts Blockchain Security in Discrepancy Detection Protocols
This section focuses on the key security parameter—primary committee size—within the Discrepancy Detection (DD) protocol for...

Exploring Cutting-Edge Approaches to Iterative LLM Fine Tuning
Section 6 – Related Work dives into various AI training approaches, categorizing them by whether they...

The Voices That Inspire HackerNoon
2 weeks left to participate in the HackerNoon survey and win big prizes! Today, let's look...

Who Owns AI Art? A Deep Dive into Copyright, Intellectual Property, and Liability
Artificial intelligence is changing the way we think about art. ChatGPT, DALL·E, and Midjourney all use...

Abhaya Uprety is Reshaping Parking One Line of Code at a Time
Abhaya Uprety co-founded ParkStash, a startup that makes parking reservations work in a way similar to...

How Transaction Order Finality Drives Blockchain State in Layer 2 Systems
The paper emphasizes transaction order finality as key to determining blockchain state. It outlines different finality...
Building a Game with AI: Fast, Flawed, and Full of Potential
Cursor is an AI coding assistant that can be used by developers to speed up their...

Prompt Injection Is What Happens When AI Trusts Too Easily
Prompt Injection is a top threat to GenAI Large Language Models (LLMs) applications. Tips on how...

AI That Trains Itself? Here's How it Works
The experiments evaluate the DNO algorithm (specifically, DNO-Prct) using an iterative training process that combines GPT-4-Turbo...

Finally, a Way to Run Your Shopify Store Without Clicking Yourself Into Madness
ShopCTL lets you easily manage your Shopify store via the command line, offering quick commands to...



