~hackernoon | Bookmarks (1959)
-
The Web3 Identity Crisis - Corporations in Decentralized Clothing
Today, I want to examine another concerning trend in the blockchain space, the growing disconnect between...
-
AI and the Dark Art of Social Engineering
AI is revolutionizing cybercrime, with deepfakes, voice phishing, and AI-generated phishing scams driving a 442% surge...
-
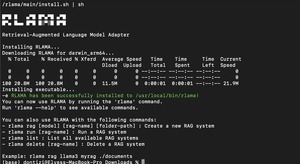
Build a Fully Local RAG System with rlama and Ollama—No Cloud, No Dependencies
rlama enables a fully local, privacy-first RAG system with no cloud dependencies. This guide walks through...
-
Artificial Intelligence Optimization (AIO): The Next Frontier in SEO
Artificial Intelligence Optimization (AIO) is one of the newest developments in search engine optimization. AIO combines...
-
The Future of Healthcare: How It Can Be Used to Save a Few Billion Lives
A lot of the diagnosis process sometimes feels like guesswork to me. Doctors have to rely...
-
OTel Me Why: Why I'm So Excited About OTel
Someone asked me why I was so excited about OpenTelemetry. The reasons have more to do...
-
Navigating the Murky Waters of AI and Copyright Law
The ongoing debate about the authorship and ownership of generative content is intense. There are two...
-
AI Won't Replace Me Yet, But It Might Prove I Was Never That Original
AI won’t replace me yet. But what if it proves I was never that original? This...
-
Building a Bitcoin Wallet from Scratch: Two Months of Solo Development Insights
Nummus will be a custodial wallet that offers a BTC-backed credit card, collateralized loans, and secure...
-
Like Kermit Once Said: “It’s Not Easy Being Green” - AI Environmental Equity
A few months ago, I spoke with Shaolei Ren, as associate professor of computer science at...
-
AutoResponder AI: The Smart Way to Manage Your Gmail Inbox
AutoResponder AI is an AI-powered email assistant that can help you save time and prevent your...
-
Linear Attention and Long Context Models
Linear Attention variants optimize autoregressive modeling with kernel approximations and efficient normalization. Long-context models promise scalability,...
-
State Space Models vs RNNs: The Evolution of Sequence Modeling
SSMs integrate selection mechanisms and state expansion to outperform traditional RNNs in sequence modeling. Models like...
-
How AI Chooses What Information Matters Most
Selection mechanisms refine AI’s approach to gating and hypernetworks, enabling structured state space models (SSMs) to...
-
The TechBeat: Is the U.S. Secretly Accumulating Bitcoin? (3/15/2025)
How are you, hacker? 🪐Want to know what's trending right now?: The Techbeat by HackerNoon has...
-
The Future of Automated Security Testing
With vehicles becoming more software-defined, the need for higher quality and more automated security testing is...
-
Our Testing Platform Can Enable a Researcher to Rapidly Establish and Experiment With ECU Networks
We now discuss how our testing platform can enable a researcher to rapidly establish and experiment...
-
Enabled Testing Methodologies: Secure Development Lifecycle (SDL) Testing and Penetration Testing
VSEC Test aims to integrate all methods of vehicle cybersecurity testing into a single easy-to-use platform.
-
Our Testbed Setup: Sourcing ECUs, Configurable Network, and Network Simulation
In the context of this work, we define ECUs as production ECUs from the field, engineering...
-
A Shipper, Not a Prototyper - A Reflective Writing and a Cover Letter
The designer, Marcio agrees that he is not a prototyper, that he is a shipper. With...
-
Angular Signals Are A Game Changer: How They're A Great Fit For Scalable Apps
*Signals* are a new concept in Angular that plays well with reactive programming and templates. They...
-
The Markup: How We Won the 2023 Media Literate Media Award
NAMLE specifically recognized The Markup for creating actionable journalism for the public good. In late 2022,...
-
Is It Risky to Live Near a Nuclear Power Plant?
A Michigan nuclear power plant is reopening as the U.S. continues looking to nuclear to solve...
-
Crafting Multi-Cloud Systems: How Tech Experts Are Solving Connectivity
Multi-cloud strategies optimize performance but pose security and connectivity challenges. Experts like Arun Pandiyan Perumal use...